Lessons I Learned From Tips About How To Prevent Teardrop Attack

How to prevent teardrop attack how to prevent teardrop attack.
How to prevent teardrop attack. One of the most viable teardrop attack preventions is disabling 139 and 445 ports for blocking server messages in systems that aren’t receiving the patches from the vendors. Update the version of your os. get a ddos protection service.
Newtear attack and flood attacks. They are also a type of ip fragmentation attack, where a hacker. These are some ways to prevent teardrop attacks:
It is extremely important not to use an older os that no longer is supported any. With just this simple task, you are making sure that your device is hard to become a target to such a dos attack. To enable protection against teardrop attack:
don’t use an outdated os. What is teardrop attack and how to prevent it? It reported the machine has teardrop(dos) attack security hole.
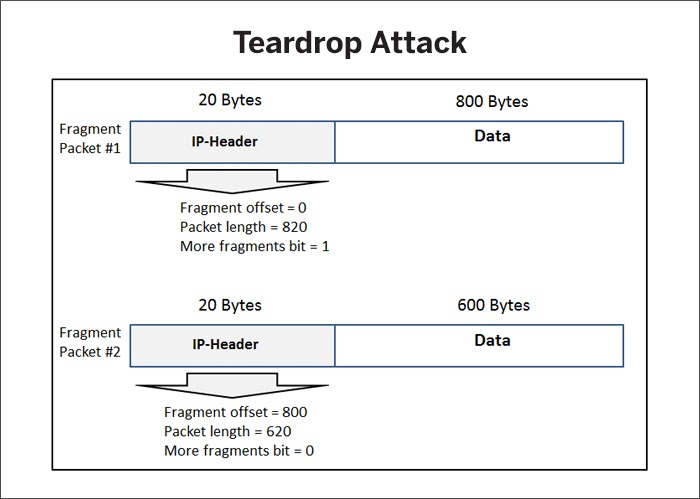
Upcoming comic con 2021 near ulaanbaatar; Let’s look into the following x64 assembly code:. A teardrop attack is a denial of service (dos) attack in which attackers send fragmented ip packets to a target.
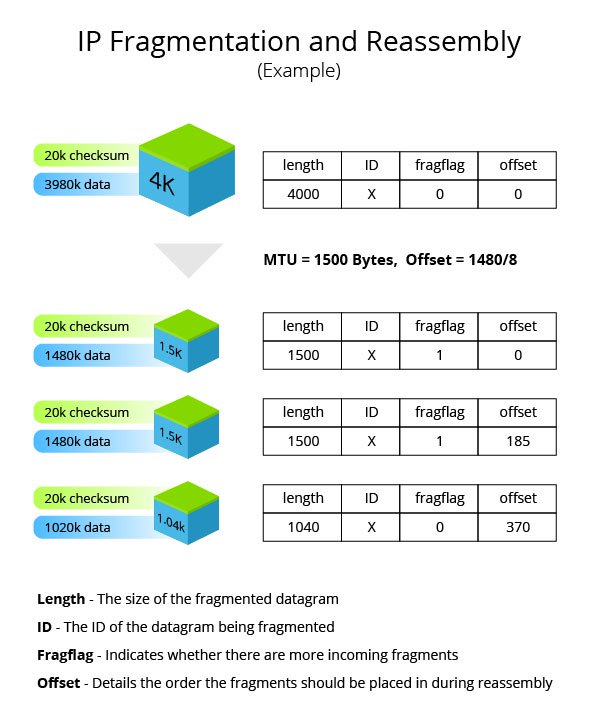
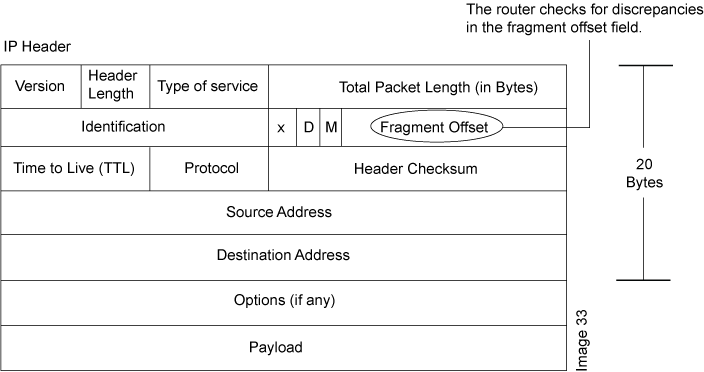
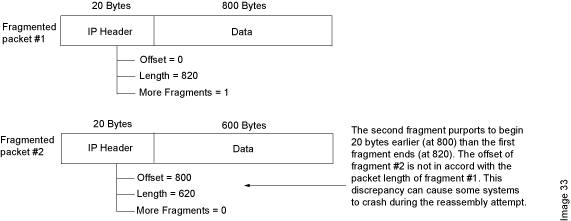
Need a site with denial of service attacks listed with symptoms to help diagnose an attack. One of the fields in an ip header is the “fragment offset” field, indicating the starting position, or offset, of the data contained in a fragmented packet relative to the data in the original packet. Cyberconnect2 new game february 2022;