Lessons I Learned From Tips About How To Prevent The Conflicker Worm
If you encounter or have encountered the win32/conficker malware, a fully updated version of an eset product (version 3.0 or later) will clean the infection.
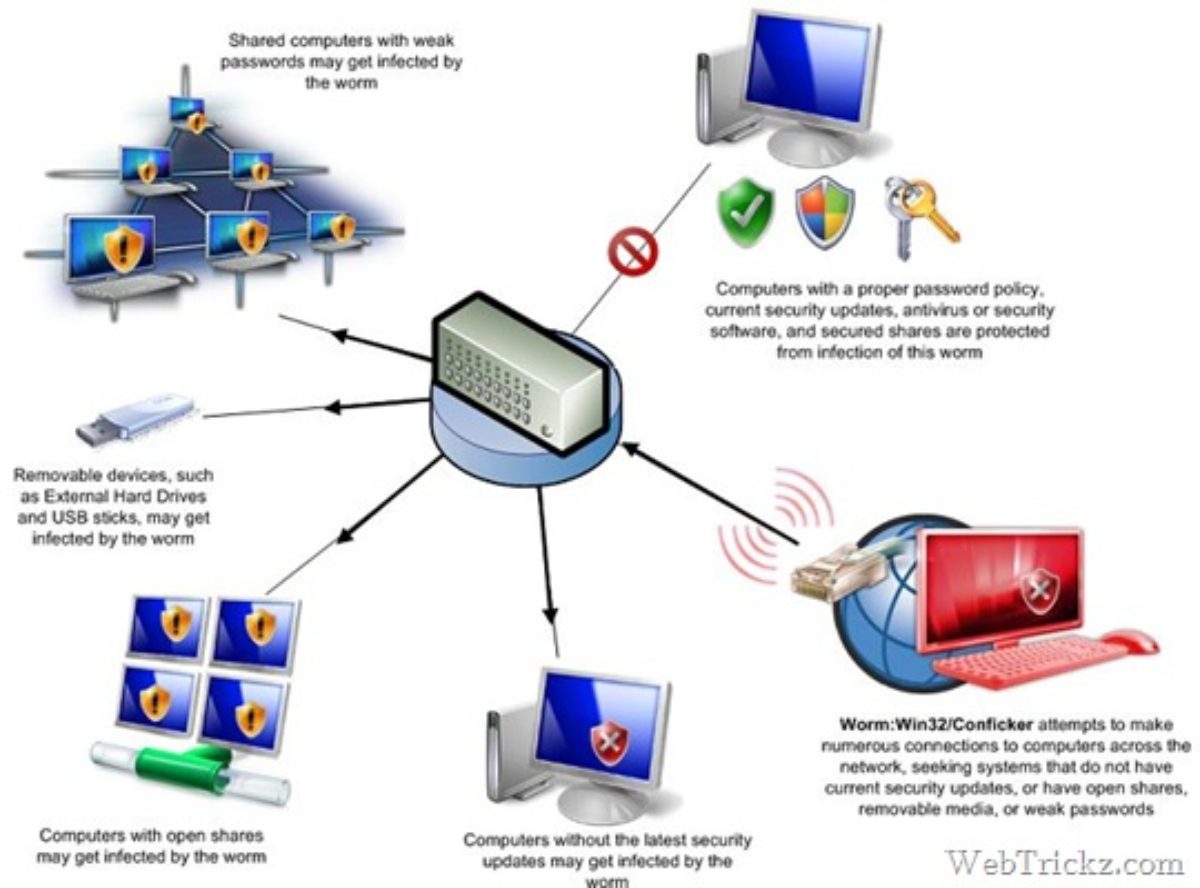
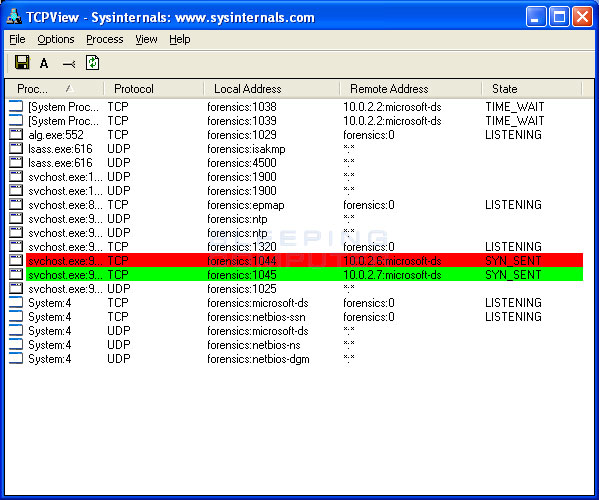
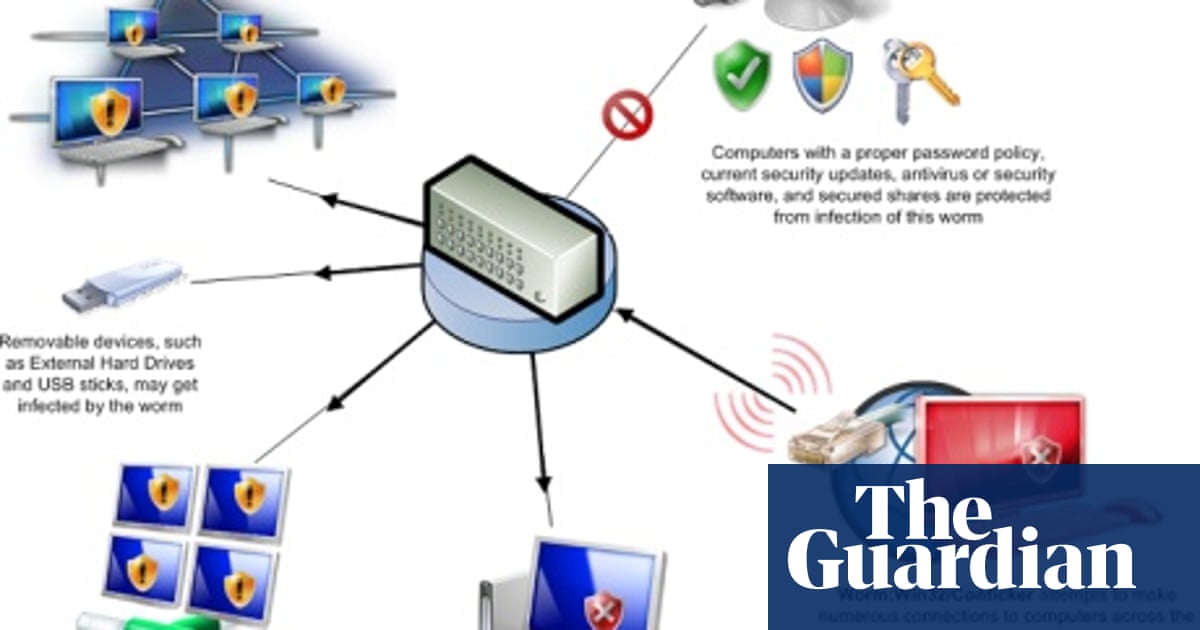
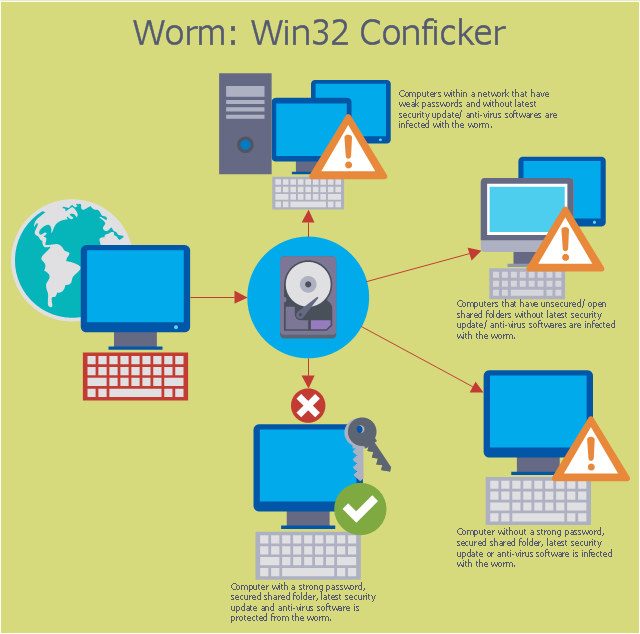
How to prevent the conflicker worm. First, the conficker worm attacks the pc through a security vulnerability that arises in windows rpc. Patch as soon as you can. If you have worm:win32/conficker!atmn kind that can barely be removed, you may require to consider scanning for malware beyond the common windows functionality.
Even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying it's not that bad, but trust me. Five steps to protecting yourself from conficker. Make sure that your operating system has the required patch installed.
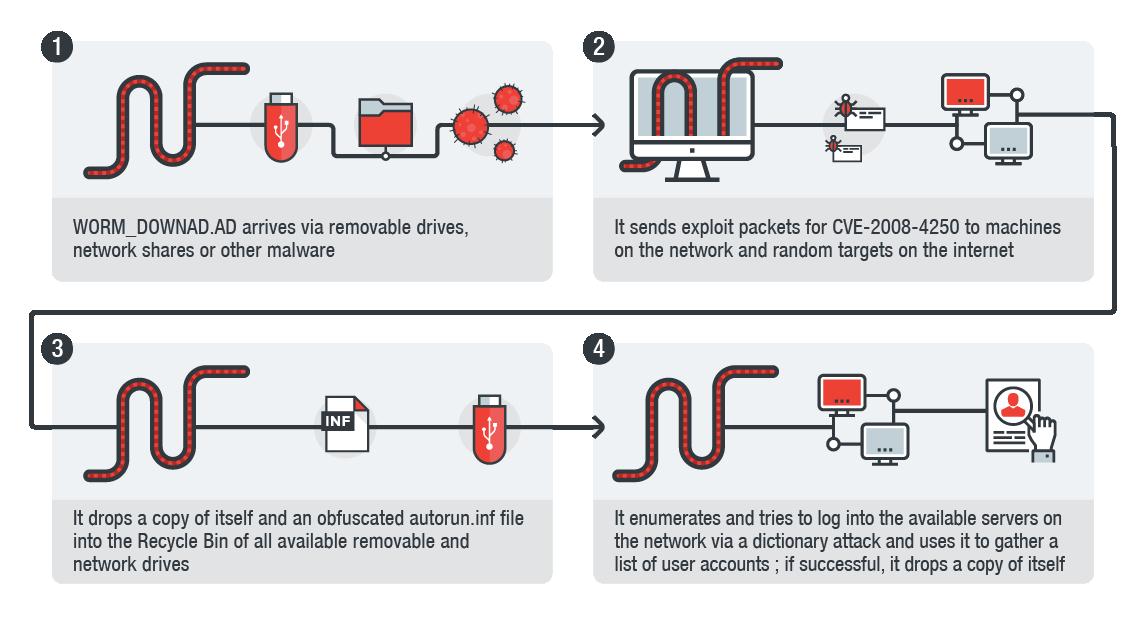
Conficker can break into pc. Graham cluley, senior consultant at antivirus company sophos inc., said: The main mode of infection of this computer worm is through usb memory sticks or an infected pc in the network that will automatically infect other pcs on par.
The microsoft malware protection center has updated the microsoft safety sca… note the microsoft safety scanner does not prevent reinfection because it is not a r… you can download the microsoft safety scanner from the following micr… see more There is a page created by the microsoft developers, who claim that if you can browse and access that, then your system. How to prevent conficker 1.
Never download software from unreliable. The conficker worm is more dangerous than other worms because it can randomly set up its file format to prevent security programs from detecting it. Run the microsoft safety scanner.
Microsoft released a removal guide for the virus, and recommended using the current release of its windows malicious software removal tool to remove the virus, then applying the patch to.